Virtual Desktop Infrastructure (VDI) in the Cloud
Not your traditional VDI. Experience a better way to engage and secure your global hybrid teams.
Tehama’s Carrier for WorkTM Platform ensures secure and compliant cloud VDI for a global workforce.
Leveraging a global workforce is riddled with security risks: from abuse of privileged credentials and data theft to legacy hardware and infrastructure constraints. Tehama mitigates these risks by establishing a secure perimeter around cloud workspaces and corporate data. Organizations are using Tehama to deploy secure desktops and applications in multiple geographies in under an hour resulting in simplified IT management and user delight.

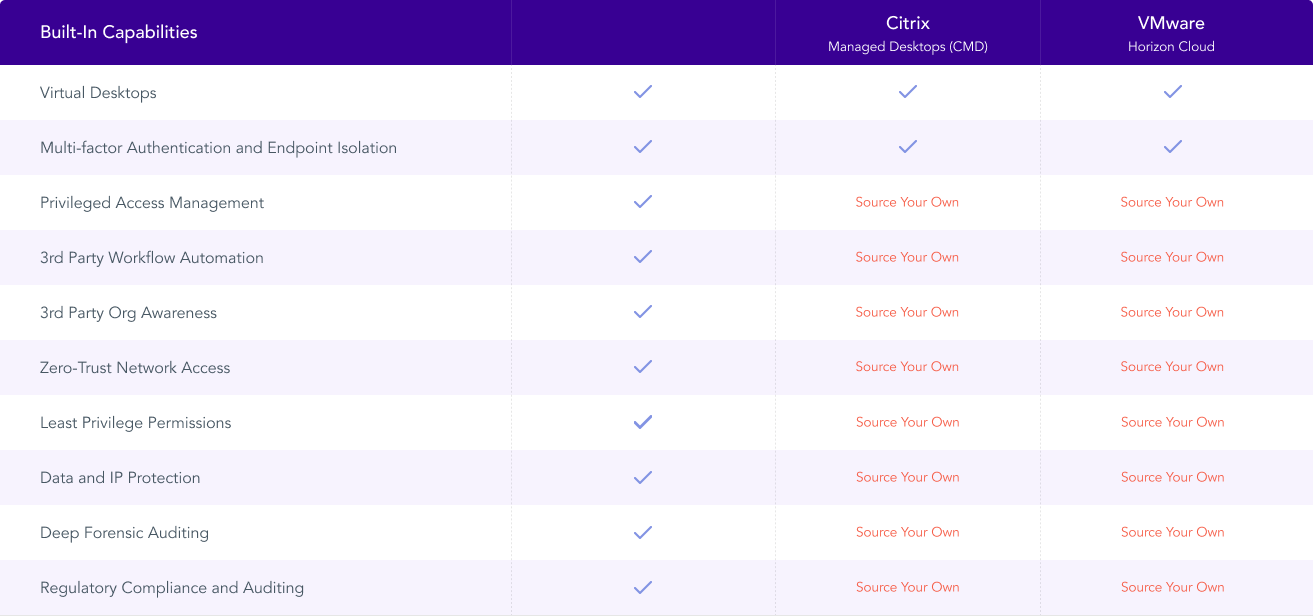
Traditional VDI Vendors vs Tehama
Traditional virtual desktop infrastructure (VDI) technology, while well established, can’t defend against a growing number of threats to your business and its corporate systems. From outside hackers, to internal human error, to compliance issues brought on by ballooning data velocities and increased regulations, traditional VDI solutions simply can’t keep up with the modern workplace.
Enter Tehama. With its VDI technology, IT teams don’t need to place controls and frameworks on managed individual laptops or other devices. And the C-suite can rest assured that Tehama’s Room Directory, Zero-trust access controls, policy controls and dynamic firewall rules help their organization meet security and compliance requirements with no integration, infrastructure or additional IT administration.
Additionally, today’s legacy Virtual Desktop Infrastructure and Desktop as a Service providers—like Citrix, VMware and Microsoft—do not offer a complete solution for securing remote work and connecting remote teams to data. With any of our competitors, you would need to integrate multiple vendor solutions to do what Tehama’s single platform does.
Enter Tehama. With its VDI technology, IT teams don’t need to place controls and frameworks on managed individual laptops or other devices. And the C-suite can rest assured that Tehama’s Room Directory, Zero-trust access controls, policy controls and dynamic firewall rules help their organization meet security and compliance requirements with no integration, infrastructure or additional IT administration.
Additionally, today’s legacy Virtual Desktop Infrastructure and Desktop as a Service providers—like Citrix, VMware and Microsoft—do not offer a complete solution for securing remote work and connecting remote teams to data. With any of our competitors, you would need to integrate multiple vendor solutions to do what Tehama’s single platform does.

Tehama is Feature Rich
1
Secure & Compliant Cloud-Based Workrooms
All the security and compliance capabilities your hybrid workforce needs in a cloud-based environment, also known as a “Tehama Workroom”. Learn more.
2
Self-service Admin Console
Manage virtual desktops with an easy-to-navigate administration console built within Tehama’s Desktop as a Service (DaaS) platform. Learn more.
3
Secure Gateway
Turn your Tehama Workroom into a secure virtual extension of your private network. The Tehama Gateway provides a secure path to data that allows remote workers to access network resources from anywhere. Learn more.
4
Desktop Intelligence and Automation (DIA)
Secure, audit and optimize all end-user devices with desktop performance and analytics monitoring. Get a complete view into the health and performance of your entire device fleet. Learn more.
5
Regulatory Compliance
Tehama takes the heavy lifting out of compliance, making it easier for your organization to meet specific regulatory requirements. Learn more.

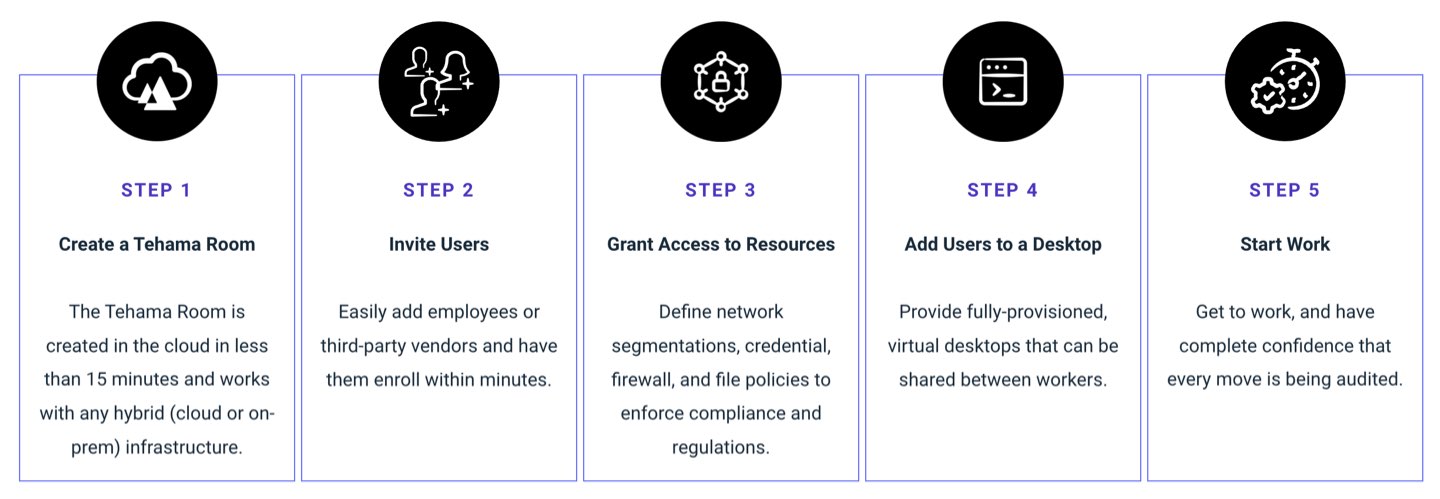
One Hour to Productivity
Tehama provides all the components required to quickly and securely onboard and manage your global workforce—improving time-to-value and scalability, while reducing downtime for users and improving the overall employee experience.
Get More Details Now
Fill out the form and we will get in touch with you to discuss your needs or book a demo.
Frequently Asked Questions
How does Tehama simplify IT management?
Tehama’s custom-built and easy-to-navigate administration console makes virtual desktop management easy with minimal IT oversight.
How does Tehama simplify IT management?
How does Tehama protect sensitive data?
The Tehama platform implements a zero-trust access model for all users, protecting sensitive data assets using tools such as segregated network access, endpoint isolation, multi-factor authentication, and least privilege permissions. These are built-in to the platform.
How does Tehama protect sensitive data?
How does Tehama provide end-users a great digital workplace experience?
Ensuring productivity is a key objective of any business. In a hybrid work norm, Tehama lets businesses transform any device whether it is corporate-issued or BYOD into a high-performance workstation for unmatched user experience. It allows hybrid workers to be productive from anywhere. Also, Tehama Desktop Intelligence and Automation (DIA) can provide key analytics around connections and performance enabling organizations to ensure the best possible experience from any location.
How does Tehama provide end-users a great digital workplace experience?
Does Tehama work on all the public cloud platforms?
The Tehama Carrier for Work ™ platform is globally available on both AWS and Oracle. Additionally, other public clouds can be used to enable the best possible user experience by running a Tehama Zero Client deployment on any cloud. Finally, the path to Data is the most important to Tehama. Leveraging any IPSEC compatible device or our Tehama Multipath gateway virtual appliance can also run in any cloud or private data center.
Does Tehama work on all the public cloud platforms?
How does Tehama compare to Azure AVD and Amazon Workspaces?
Azure AVD is VDI infrastructure on Azure. An organization would use AVD and build their own virtual desktop or Desktop as a service (DaaS) environment. Each organization would host and manage its own AVD environment or can have a managed service provider manage this custom-built environment. Amazon Workspaces is a DaaS platform organizations or partners can manage this platform. With both AVD and Amazon workspaces you still need to add security, networking, compliance, and secure connectivity to your corporate asset. You will need to repeat this each time a custom environment is built. Tehama is a complete carrier for work platform and includes all the technologies you need and it is completely managed by Tehama or our partners to enable hybrid work. It is enabled in 1 hour, and ready for use. Tehama is unique in the market.
How does Tehama compare to Azure AVD and Amazon Workspaces?
Is the product HIPAA and PCI compliant?
Tehama has built-in policy controls that enforce users to meet certain entry requirements before gaining access to a desktop or Workroom, helping organizations meet specific regulatory requirements like SOC 2 Type II, GDPR, OSFI, FIPS, 23 NYCRR 500, PCI, and HIPAA.
Is the product HIPAA and PCI compliant?

