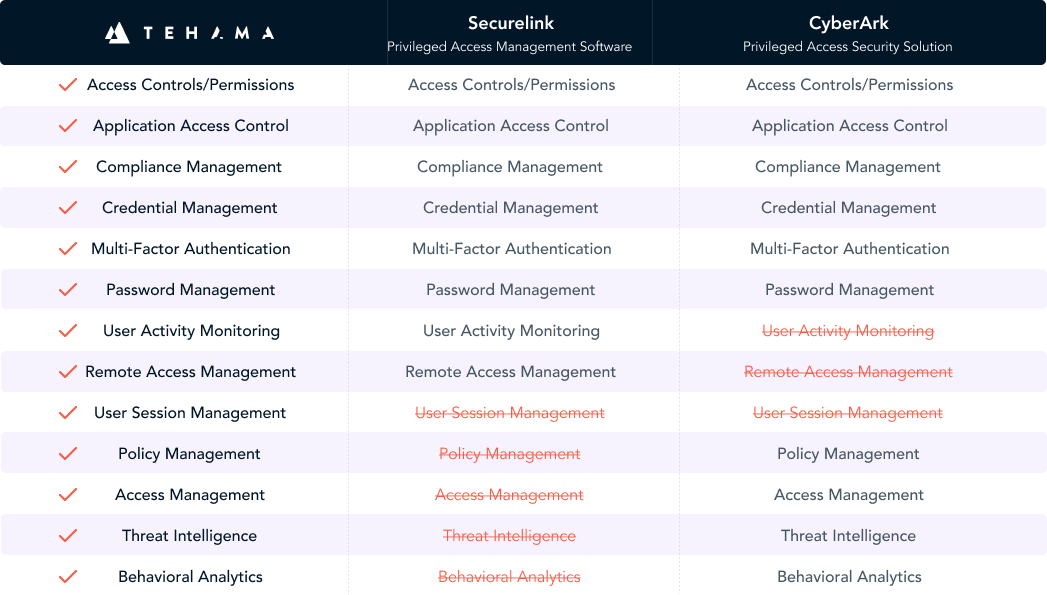
Tehama’s turnkey, cloud-native privileged access management (PAM) solution can be adopted in under an hour; offers built-in third-party workflow access automation and compliance supporting activity and event streams; and, does not require added infrastructure or licensing and management of server-side software solutions.


Gain control over privileged access.
- Privileged access can be risky. Providing remote access to application and data infrastructure creates a security risk. Tehama's built-in third-party access workflow automation and compliance-supporting activity and event streams permit a fully-secure and compliant mechanism for freelancers and service providers to access sensitive enterprise data and systems.
- Data points to a rising threat. According to a 2022 Ponemon Institute report on privileged user threats, however, privileged user attacks are on the rise and skyrocketed by 44% in 2020, with the cost per attack estimated at $15.38 million.
- Track, manage, control and simplify privileged access. Existing privileged access management solutions require organizations to license, download, install and operate server-side software and install agents on every desktop that needs to be supervised. Only the Tehama Carrier for Work™ provides a single, turnkey, fully-managed solution that provides pay-by-the-minute access and can be adopted in under an hour, using the team you already have in place.


Identify and eliminate unprotected privileged accounts.
- Protecting valuable credentials. The Tehama Carrier for Work™ eliminates the possibility of password leakage, and prevents security breaches, data leaks, and injection of malware by eliminating the need to distribute credentials through potentially insecure channels, such as email.
- Unmatched visibility and control. Administrators and managers have full control over privileged credentials, allowing organizations to grant, revoke, and track access to sensitive company assets, such as databases, in real-time.
- Situational awareness. The Tehama Carrier for Work™’s built-in PAM tools enable tracking user access so that security threats and vulnerabilities can be identified and mitigated in real time.


Provide Secure Access to Network Resources From Anywhere.
- Zero-trust security. The Tehama Carrier for Work™ is built on a zero-trust access model for all employees and third-party contractors, protecting sensitive assets with segmented network access and dynamic firewall rules.
- Audit trails and access logs. Session recordings and detailed logging through the Tehama Carrier for Work™ provides a view who is doing what within the environment, while also supporting regulations your business must comply with (like 23 NYCRR 500, GDPR, SOC 2 Type II, ISO, HIPAA, CCPA and OSFI).
- Principle of Least Privilege (POLP) enforcement. The Tehama Carrier for Work™ enforces POLP by protecting data assets in secure Tehama Workrooms that deliver data only through pixels and audio, granting global workers access only to the systems they need to perform their work.


Frequently Asked Questions
What is a privileged account and what does it do?
Privileged accounts are the foundation that enables IT professionals to manage the hardware and software used by organizations to provide access to business critical data and applications. In contrast to a user account, which usually represents a human identity, privileged accounts can be human or non-human and have elevated administrative privileges attached to them. Similar to user accounts, privilege accounts have passwords. Yet, many tools exist today that enable cybercriminals to access password-protected systems. This can be disastrous in the event that a hacker penetrates a privileged account, as it then provides them with access to an organization’s most sensitive data, enables them to distribute malware more easily, and remain undetected in the system for longer periods of time as they can bypass security controls and erase any audit trails.
What is a privileged account and what does it do?
What is privileged access management (PAM)?
Privileged access management helps organizations protect privileged accounts from cybercriminals and is inclusive of the technologies and solutions that are used to secure, control, monitor and audit access to critical data, applications and infrastructure. According to Gartner, PAM tools offer features that enable organizations to: Discover privileged accounts on systems, devices and applications for subsequent management. Automatically randomize, manage and vault passwords and other credentials for administrative, service and application accounts. Control access to privileged accounts, including shared and “firecall” (emergency access) accounts. Isolate, monitor, record and audit privileged access sessions, commands and actions.
What is privileged access management (PAM)?
What market forces are driving demand for PAM technologies and solutions?
Even in today’s most sophisticated IT environments, privileged accounts are often managed with common passwords used across multiple systems. Compounding this issue is the unauthorized sharing of credentials and failure to change default passwords, which makes these privileged accounts especially vulnerable to cyberattacks. This is evidenced by the Verizon 2022 Data Breach Investigations Report (DBIR), in which researchers found that more than 80% of attacks on an organization’s infrastructure are attributed to stolen password credentials. The study also revealed that there has been an almost 30% increase in stolen credentials since 2017, making it now one of the most “tried-and-true” methods for gaining access to an organization’s infrastructure.
What market forces are driving demand for PAM technologies and solutions?
What is the difference between Identity and Access Management (IAM) and PAM?
IAM is used by organizations to automate control of user provisioning, along with security best practices that protect all user identities. While both PAM and IAM are commonly used methods to ensure the highest levels of security are maintained when providing access to corporate data, applications and infrastructure, PAM is considered a subset of IAM, focused on providing privileged users with the permissions they need to access more sensitive data and resources.
What is the difference between Identity and Access Management (IAM) and PAM?
What sets Tehama’s PAM solution from existing PAM solutions?
Tehama is the only born-in-the-cloud, fully-managed, pay-by-the-minute PAM available today. With Tehama, organizations can adopt PAM in under an hour; gain access to built-in third-party workflow access automation and compliance supporting activity and event streams; and, they are not required to add infrastructure or licensing and management of server-side software solutions.
What sets Tehama’s PAM solution from existing PAM solutions?
What problems does Tehama solve with its PAM solution?
Providing remote access to application and data infrastructure creates a security risk. Tehama's built-in third-party access workflow automation and compliance-supporting activity and event streams permit a fully-secure and compliant mechanism for freelancers and service providers to access sensitive enterprise data and systems. Further, Tehama eliminates the possibility of password leakage, and prevents security breaches, data leaks, and injection of malware by eliminating the need to distribute credentials through potentially insecure channels, such as email.
What problems does Tehama solve with its PAM solution?
See How it Works
Tehama’s integrated Privileged Access Management offerings can give you peace of mind that comes from knowing your critical applications and data are protected with the Tehama Carrier for Work™.
What is the Tehama Carrier for Work™?
Tehama is the only all-in-one platform that lets enterprises launch role-based, ready-to-work, secure cloud work environments for anyone, on any device anywhere in the world - in under an hour. Onboard your hybrid workforce in less than an hour with built-in multi-level security and compliance. Keep your data safe and your workforce productive.
Learn moreX

