Enterprise Desktop-as-a- Service

Tehama’s enterprise Desktop-as-a-Service (DaaS) platform provides better endpoint security, but for less cost and with far greater flexibility than traditional DaaS solutions.
Tehama’s first-of-its-kind DaaS solution eliminates endpoint security concerns while simplifying and speeding up the provisioning of a global workforce. Get a globally distributed team up and running in minutes – no matter where they’re located – while keeping corporate systems and IP locked down through secure virtual rooms and desktops featuring automated, out-of-the-box monitoring, auditing and credential management tools.

Enter Tehama. With its trailblazing technology, IT teams don’t need to place controls and frameworks on managed individual laptops or other devices. And the C-suite can rest assured that Tehama’s Room Directory, zero-trust access controls, policy controls and dynamic firewall rules help their organization meet security and compliance requirements with no integration, infrastructure or additional IT administration.
Additionally, today’s legacy VDI and DaaS providers—like Citrix, VMware and Microsoft—do not offer a complete solution for securing remote work and connecting remote teams to data. With any of our competitors, you would need to integrate multiple vendor solutions to do what Tehama’s single platform does.
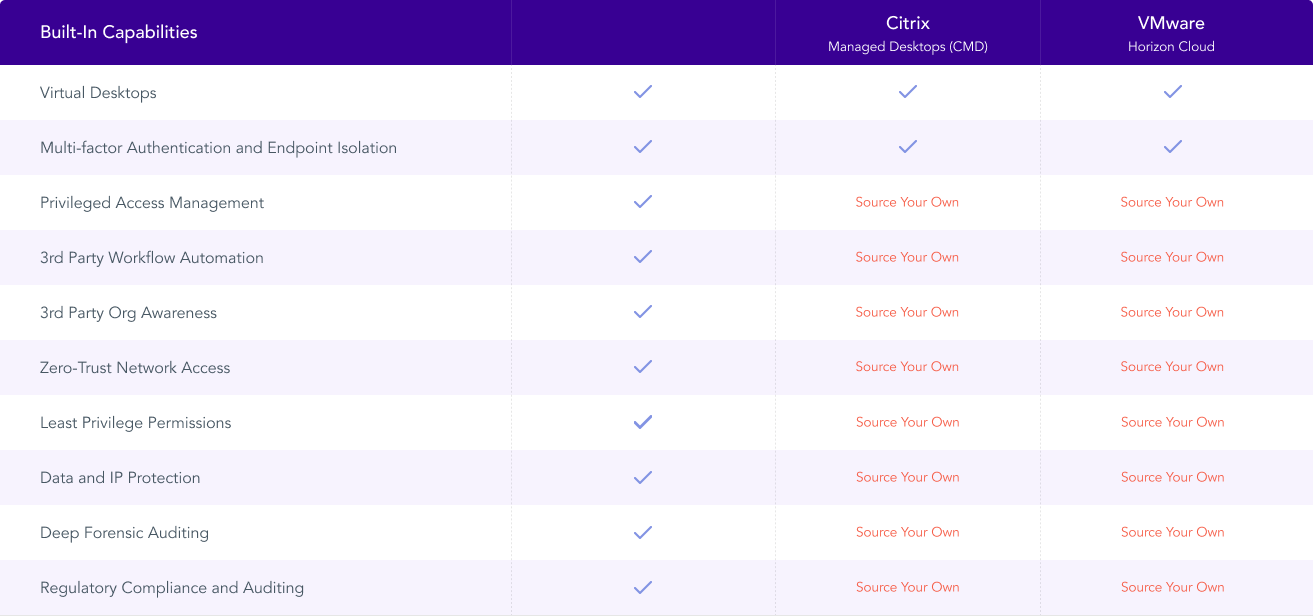

Deploy 1 to 10,000 secure & compliant virtual desktops anywhere in the world, in minutes.
There’s no getting around it: traditional DaaS is little more than an unmanaged cloud-based operating system (OS) that typically needs a lot of babysitting. For a DaaS model to be secure and compliant, IT teams need a battery of complex controls and frameworks placed on each endpoint device – not exactly a formula for nimble provisioning across multiple continents.
With Tehama’s Enterprise DaaS platform, you can deliver one, 10, or 10,000 virtual desktops across the globe in minutes and keep them running seamlessly for a day, a week, a month, or indefinitely. It provides the same or better network capabilities as a traditional DaaS model, along with world-class security mechanisms and controls that can be rolled out at scale – and scaled-down, if necessary, just as quickly.

Tehama for Better Business Outcomes
Onboarding (& Offboarding) Global Teams




