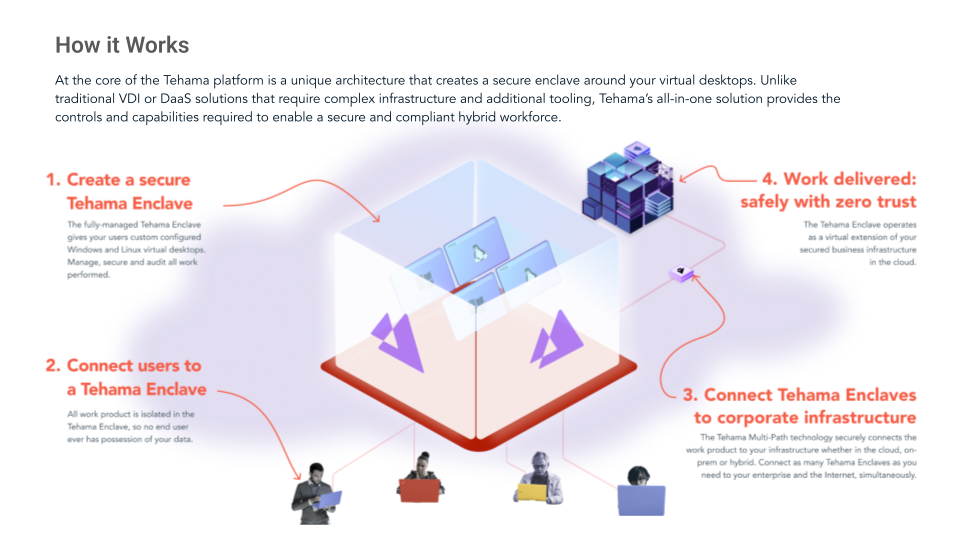
What is a Tehama Enclave?
- Zero-Trust Network and Endpoint Isolation. The Tehama Enclave is built on a zero-trust access model. Protect all data with policy-based access controls, multi-factor authentication, and a Secrets Vault for privileged access management.
- Segmented Network Access. Grant global workers access to only the systems and information they need. Eliminate cross-network access typical of VPNs.
- Assign Enclaves Based on Department or Region. Create Enclaves for various departments or project needs. Set a Enclave for specific geography to help comply with data sovereignty requirements.

Protect Sensitive Data
Enforce enterprise-grade security controls without any added tooling, infrastructure, or IT administration. You control what enters the Enclave, and what leaves.
- Data and IP Protection. Keep data and intellectual property safe from breaches and abuse. Easily manage and track any asset accessed on-premises or by remote employees, contractors, and vendors.
- Secure File Sharing. Share files between virtual desktops to facilitate secure collaboration. Track who has accessed which files, and prevent any sensitive data from leaving the Enclave.
- Group Policy Management. Centrally manage all critical updates and security settings across desktops. No need to make manual changes or re-image desktops.
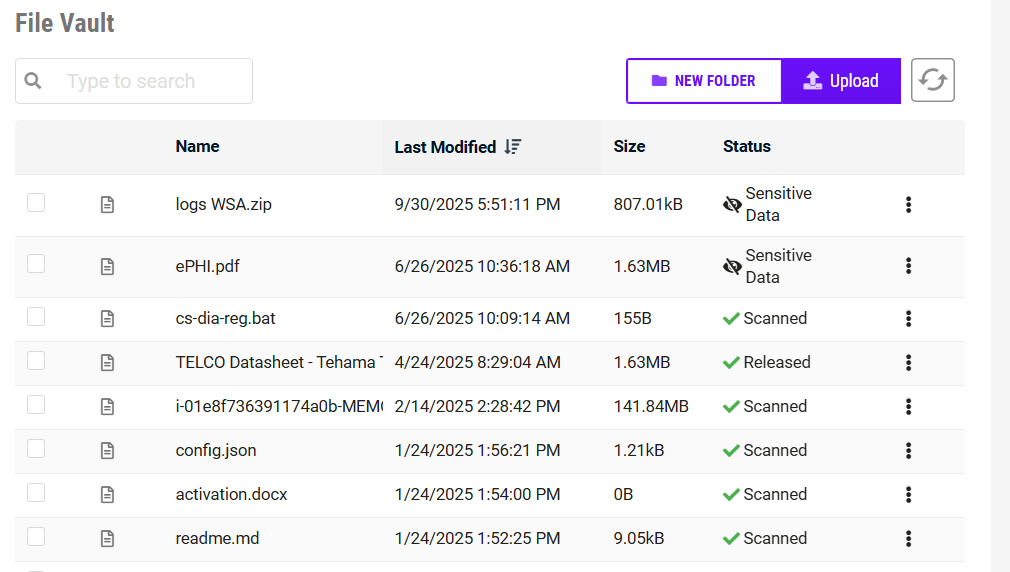

Easily Audit All Work and Achieve Regulatory Compliance
Built-in auditing tools help you meet your industry’s compliance requirements.
- Session Recordings. Securely capture all activity within a desktop through recorded sessions. Provide hard evidence for regulators to prove compliance.
- Audit Trail and Access Logs. Track everything that happens within a Tehama Enclave Activity Stream. Monitor which users have access, to what, and for how long.
- Compliance Frameworks. Activate security and compliance controls that meet even the most stringent compliance frameworks, including SOC 2 Type II, CMMC, ISO 27001, FIPS, PCI, and HIPAA. See All Compliances

Protect Sensitive Data and Eliminate
Endpoint Security Concerns.
Endpoint Security Concerns.
Find out how Tehama can help you deploy
secure cloud desktops in 3 simple steps.
secure cloud desktops in 3 simple steps.
Read How Tehama Has Enabled Systems Integrators to Validate the Trust of the World’s Most Demanding Public-sector Clients.
The organization now has a cost-efficient solution that eliminates delays in vendor onboarding while providing full visibility and unparalleled SOC 2 security in a cloud-based desktop environment.
Go to Case Study

