Go Beyond Virtual Desktops with
Tehama's All-in-One Platform.
Fully loaded with all the Security, Risk Management, Automation, Remote Access, and Flexible Licensing You Need to Empower Your Global Teams.
How it Works
At the core of the Tehama platform is a unique architecture that creates a secure perimeter around your virtual desktops. Unlike traditional VDI or DaaS solutions that require complex infrastructure and additional tooling, Tehama’s all-in-one solution provides the controls and capabilities required to enable a secure and compliant hybrid workforce.
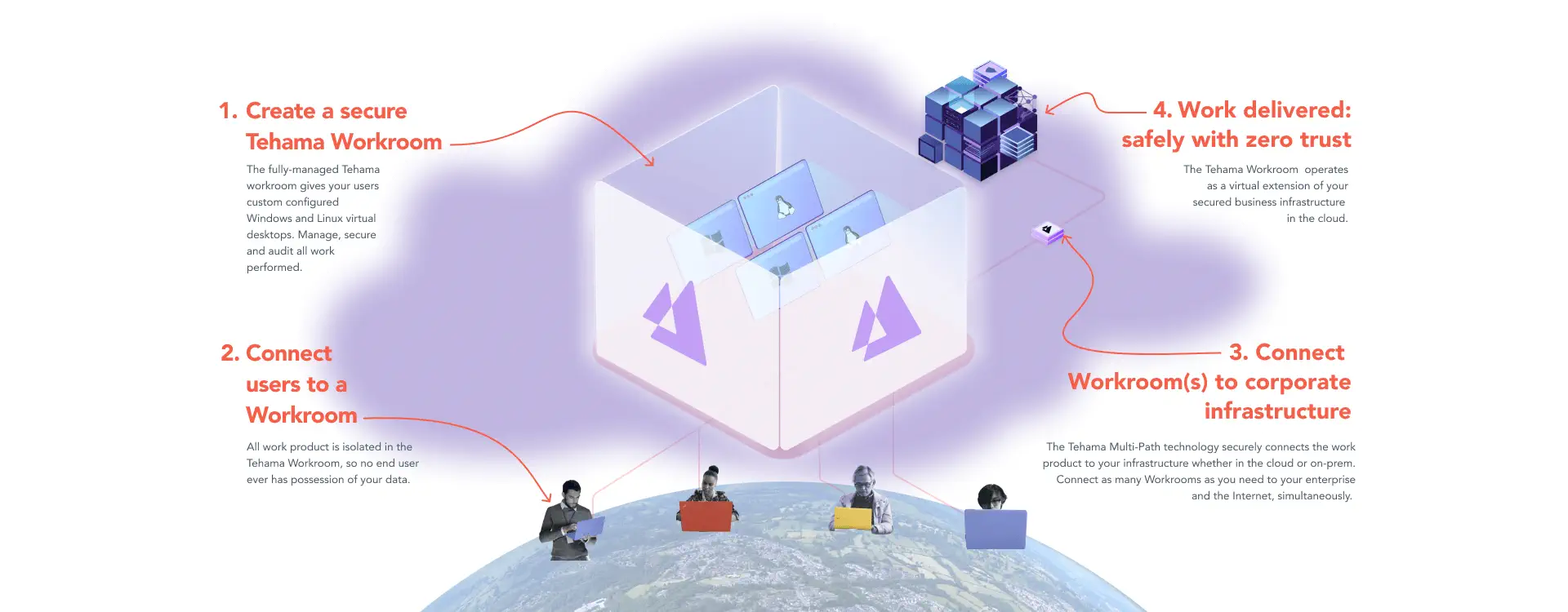
All The Features You Need

Tehama vs Our Competitors
Today’s legacy VDI and DaaS providers—like Citrix, VMware, and Microsoft—don’t offer complete solutions for securing hybrid work or connecting remote teams to data.
Tehama takes the guesswork out of building a hybrid work infrastructure. You can sleep well knowing you have all the features you need to keep your data safe.
Tehama takes the guesswork out of building a hybrid work infrastructure. You can sleep well knowing you have all the features you need to keep your data safe.
Built-In Capabilities

Citrix
Managed Desktops (CMD)
VMware
Horizon Cloud
Virtual Desktops
Multi-factor Authentication and Endpoint Isolation
Privileged Access Management
Source Your Own
Source Your Own
3rd Party Workflow Automation
Source Your Own
Source Your Own
3rd Party Org Awareness
Source Your Own
Source Your Own
Zero-Trust Network Access
Source Your Own
Source Your Own
Least Privilege Permissions
Source Your Own
Source Your Own
Data and IP Protection
Source Your Own
Source Your Own
Deep Forensic Auditing
Source Your Own
Source Your Own
Regulatory Compliance and Auditing
Source Your Own
Source Your Own
Would you like more information?
Drop your details in the form and a member of the Tehama team will be in contact with you to discuss your needs or get a demo.
See what others are saying about Tehama's game-changing technology























